Turn on Multi-Factor Authentication Now
Do it before the hackers do it for you

In This Article
• Passwords are an open door for hackers
• What is multi-factor authentication?
• How do we count authentication factors?
• Examples of multi-factor authentication
• What's the urgency?
(No time to read right now? Just want to see the list of things to know? Here you go.)
Introduction
 The most common way hackers get into your online accounts is by guessing your password. They use software that tries thousands of passwords every second.
The most common way hackers get into your online accounts is by guessing your password. They use software that tries thousands of passwords every second.
Many people do not use long and strong passwords. You can test your password strength and see if any of your online accounts have been breached. (These sites are safe to use and do not save your password or email address.)
We know that coming up with (and remembering) good passwords is hard.Check out this article with tips to make it a lot easier.
But even if you use a good password, hackers can use a “man in the middle” attack to capture it and then use it later to log into your account.
So it's critical that you use an extra layer of protection whenever it's available.
It's called “two factor authentication” (abbreviated as 2FA) or “multi factor authentication” (abbreviated as MFA).
How Do We Count Authentication Factors?
Authentication factors are ways you “prove you're you” and are things like…
Something you know (such as a password or your mother's maiden name)
Something you have (such as cellphone that just got texted a 6-digit code)
Something you are (such as your fingerprint or face)
Using just one factor isn't secure enough. Two (or multi) factor authentication provides an additional barrier to hackers.
Examples
Examples of two factor authentication include…
You provide your username and password to a website login page (one factor), then the site texts a code to your phone (a second factor) to complete the login process.
As part of its login process (one factor), a site requires you to provide the code from an authenticator app (a second factor) on your phone.
To unlock a company-issued laptop, you enter your username and password (one factor), then put your finger (a second factor) on a fingerprint reader pad.
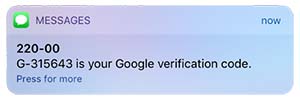 It's important to understand that using a code texted to your phone or using an authenticator app are not completely unhackable — there are ways even those methods can be circumvented by clever hackers.
It's important to understand that using a code texted to your phone or using an authenticator app are not completely unhackable — there are ways even those methods can be circumvented by clever hackers.
You still need to be careful about where you provide your username and password.
For example, if a hacker can trick you to click a link in a phishing email that goes to a page he controls, he can not only capture your username and password, but possibly your second factor authentication code as well.
What's the Urgency?
 Hackers are constantly probing people's online accounts.
Hackers are constantly probing people's online accounts.
If they're able to get into one that has 2FA / MFA available but not turned on, they will sometimes enable it using a new email address they create.
This is like someone picking the lock to your house and then changing the lock — it's still on your house, but now they have the key and you don't.
A good resource that shows which websites offer 2FA / MFA is twofactorauth.org.You can click a category or search for a particular website.
Most large websites offer 2FA / MFA and you should enable it whenever possible.
In addition, you should be wary of sharing credit card information on any site that does not offer that feature because it indicates they do not take security seriously enough.
 Luckily, it's easy to set up 2FA / MFA and you only have to do it once per site. Some sites send you an initial security code that you provide back to confirm.
Luckily, it's easy to set up 2FA / MFA and you only have to do it once per site. Some sites send you an initial security code that you provide back to confirm.
For sites that use an authenticator app, you just take a picture of a QR code which initializes the process.
Summary
Yes, using 2FA / MFA is an extra step you need to take. But don't you feel safer having a deadbolt lock on your door in addition to the regular (and probably weaker) lock?
Questions?
If you have any questions about anything here or if there's an issue you'd like us to write about please get in touch.
Want More Info Like This?
Get our Free Newsletter
