Fake Tech Support Scams (and how to avoid them)

In This Article
• The hacker's goals
• How the scams work
• The hacker's bait and methods
• Warning signs
• Your best defense
• Already got scammed?
(No time to read right now? Just want to see the list of things to know? Here you go.)
Introduction
In these scams, a hacker fools a victim into thinking something is wrong with his computer, then offers bogus assistance for a fee.
Fake tech support scams have been around for years and, unfortunately, still trick people into handing over money, having malware installed on their computer, or having financial and other personal files stolen.
By using the latest technology in deviously clever ways, scammers can hide their tracks and avoid getting caught.
With increased awareness of cybersecurity issues in recent years, people are rightly concerned about their home computers.
Luckily, you're about to learn how to spot these scams and avoid becoming a victim.
The Hacker's Goals
The hackers who carry out these scams have a few goals:
Get you to pay for something you do not need (by fixing a problem you don't have or making you sign up for a security subscription you don't need)
Install malware (viruses and other nasty stuff) on your computer
Install “remote access backdoors” on your computer so they can connect to your computer later without detection
Steal your financial or other personal information
In the cases where they're trying to get your money, they typically do it a few ways.
 They may ask you to buy gift cards and send them a photo of the card and its PIN. They may ask you to send money via a money transfer app like Venmo, Zelle, or the Cash App. Or they may ask you to send them prepaid cards from Visa, Mastercard, or American Express.
They may ask you to buy gift cards and send them a photo of the card and its PIN. They may ask you to send money via a money transfer app like Venmo, Zelle, or the Cash App. Or they may ask you to send them prepaid cards from Visa, Mastercard, or American Express.
Scam Summary - How it Works
The hacker triggers something to get the victim to take action
The victim calls the hacker, thinking it's a legitimate company
The hacker gets remote access to the victim's computer
He points out a technical problem
He offers a solution that requires a fee
The victim pays the fee
Best case scenario:
— The hacker just takes the victim's money
Worst case scenario:
— The hacker takes his money, steals financial info, and installs malware
The Hacker's Bait
There are several ways that hackers bait victims into falling for their scams. These can include phone calls with a fake Caller ID name, popup windows on your computer, or phishing emails.
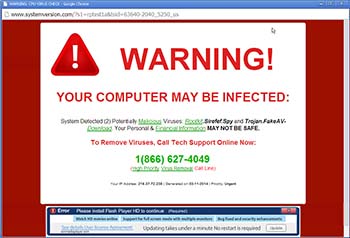 They can also include fake websites the hackers get to show up in search engines when people look for tech support. And sometimes the hackers even run online ads targeting people looking for technical help.
They can also include fake websites the hackers get to show up in search engines when people look for tech support. And sometimes the hackers even run online ads targeting people looking for technical help.
To add apparent legitimacy to their scams, hackers will often make it look like they work for companies like Microsoft, Google, Apple, Facebook, Amazon, or PayPal.
Scamming Methods
When someone takes the bait, the hackers do some things to reel in the victim. They provide a toll-free number, they stress the urgency of the problem, and they scare the victim into thinking that vital personal information will be lost if he doesn't call in right away.
Once the victim calls, the hacker sets up a remote access session to the victim's computer. He'll then run a “diagnostic” test which will show some problems.
Diagnostics - Real or Not Real?
In both the Windows and MacOS operating systems, there are legitimate diagnostic tests that will appear to show a lot of scary things, but in reality are just normal system activities that are not of any concern.
While the diagnostic test is running, the hacker secretly will be doing one (or several) things. These include scanning your computer and stealing files, photos, and financial info; installing viruses and other malware; and setting up a remote access backdoor so he can gain access later without your knowledge.
When the test is done, the hacker will show you things that look like problems but aren't (see box). He'll then persuade you to pay him to fix it and/or buy a security software subscription (neither of which will be legitimate).
Warning Signs
To avoid becoming a victim, there are warning signs to look out for.
First, reputable companies are not remotely monitoring your computer for problems and they won't call, text, or email you to report a problem.
Second, if you're running legitimate antivirus software and it detects a potential problem, it will not ask you to call a phone number.
Third, no valid company wants to be paid via gift cards or money transfer apps.
If you see any of these warning signs, be very cautious.
Your Best Defense
To defend yourself from these scams, keep the following in mind…
If you get an unsolicited call about a problem, just hang up.
Be very wary of unsolicited emails, texts, or popup windows warning you about a problem.
Don't trust emails just because they have a logo from a well-known company — those are easy to fake.
Never click links or open attachments in an unsolicited email about a problem.
Never give anyone remote access to your computer unless you initiated the contact and are 100% sure they're legitimate.
Use good, legitimate antivirus software from well-known security companies.
— Make sure to keep it updated and run it on a regular basis.
— Mac users: You are not immune to viruses! (Get in touch for recommendations on Mac antivirus software.)
If you think you have an actual tech problem, go to someone you know and trust or to a local store that sells computer equipment and offers tech support.
If you have a problem with a specific software app, contact its manufacturer directly via their website.
— Make sure to spell it correctly: scammers often set up fake websites using common misspellings of company names.
Don't Google the name and click on the first link or a link that says "Ad" - those are sometimes not legit.
What if You Already Got Scammed?
If you think you may have been a recent victim of a fake tech support scam, don't panic. You can try these things:
If you paid via a debit or credit card, contact the bank or credit card company immediately and try to stop the transaction
If you paid via a gift card, contact the issuer and ask if they can refund your money
If you gave a scammer remote access to your computer, make sure your security software is up to date, then run a full system scam
if you provided a username and password to a scammer, change your password immediately to a strong one. If you use the same password in multiple places, change it there, too.
Report scams to the Federal Trade Commission (FTC) so they can build a case against the scammers
Summary
The hackers that run fake tech support scams are clever and ruthless. They're aware that many people are concerned about computer security. And they know ways to trick people and have no moral about causing harm.
However, there are clues and warning signs you can watch out for. Stay vigilant and don't be a victim.
Questions?
If you have any questions about fake tech support scams, please get in touch...
Want More Info Like This?
Get our Free Newsletter
